Azure AD as IdP with AD FS as RP
June 16, 2013
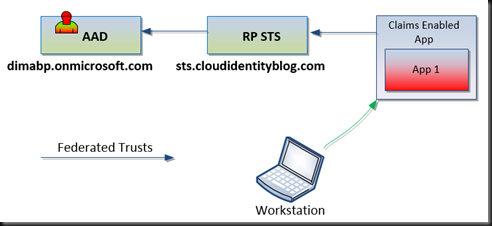
A few weeks ago I mentioned that I’d like to do a series of posts about different topologies and capabilities with claims based authentication. Well, I decided to start with one of the last from the list and show how we can use Azure Active Directory (AAD) as Identity Provider with AD FS being a Relying Party.
This demonstration shows the following topology:
User gains access to the claims enabled application with his identity coming from the Azure Active Directory. For better viewing experience make sure HD is ON and view it in full screen.
Azure Active Directory as IdP and AD FS as RP from Dmitrii on Vimeo.
Comments? Leave it below.
Can we link the claim-based app directly to AAD or must we have ADFS in between?
LikeLike
yep, you can, aad online documentation provides examples of how to do that.
LikeLike
Thanks for your answer. So next question linked to this one 🙂 What the point of having ADFS there if you pass all the claims “as-is” (except that you could change them if needed?). Maybe does that allows to have a SSO (I’m thinking to the case where I’m in a hotel, using the login form of ADFS proxy) between an application linked to AAD and another one to our on premise STS?
I forgot to say thanks for the video, so I say it now: thanks for the video 🙂
LikeLike
The point is that not all applications will be configured with AAD, many apps already configured in some type of topology, potentially with multiple Identity Providers. Ability to add AAD as IdP to ADFS allows us to use those apps with accounts hosted in AAD, with very little to no changes made in the app itself. I think I need to make a short post about it, maybe later today.
LikeLike
I followed your instructions, went to AAD, logged in and got:
“Sorry, but we’re having trouble signing you in.
Account ‘xxx@yyy.onmicrosoft.com’ is not configured to sign-in to this application”
Is there anything else that has to be configured on the tenant?
LikeLike
hmm, not sure, do you get that error as you were signing into the WAAD?
LikeLike
Yup.
Looking at the error again, I noticed that there is an error message on the bottom right-hand side of the screen – faint font so easy to miss – basically that the RP wasn’t defined.
The problem was that the adfs/ls part is https but the services/trust part needs to be http.
All OK now.
Many thanks.
LikeLike